L2TP is preferred over PPTP for building VPN networks, mainly for security and higher availability due to the fact that one UDP session is used for data and control channels. Today we will look at setting up an L2TP VPN server on a Windows server 2008 r2 platform.
PPTP
Point-to-Point Tunneling Protocol is a protocol invented by Microsoft for establishing VPNs over dial-up networks. PPTP has been the standard protocol for building VPNs for many years. It is only a VPN protocol and relies on various authentication methods for security (the most commonly used is MS-CHAP v.2). Available as a standard protocol on almost all VPN-enabled operating systems and devices, allowing you to use it without the need to install additional software.
Pros:
- PPTP client is built into almost all operating systems
- very easy to set up
- works fast
Minuses:
- insecure (vulnerable authentication protocol MS-CHAP v.2 is still widely used)
L2TP and L2TP/IPsec
Layer 2 Tunnel Protocol is a VPN protocol that by itself does not provide encryption or privacy for traffic passing through it. For this reason, the IPsec encryption protocol is typically used for security and privacy.
Pros:
- very safe
- easy to set up
- available on modern operating systems
Minuses:
- slower than OpenVPN
- additional router configuration may be required
And so back to the settings for deployment VPN L2TP Servers we will be using Windows Server 2008 R2, however, with minor modifications, everything that has been said will also be true for other versions of Windows Server.
We need an installed role, which should contain how to do this, we described in detail in the previous article where we raised PPTP VPN, therefore, I see no point in describing this process again, further we will assume that the role Network Policy and Access Services you have already installed and contains Routing and Remote Access Services. General deployment VPN L2TP Servers very similar to deployment PPTP VPN, with the exception of a few settings, which we will discuss in detail.
Go to Server Manager: Roles -Routing and remote access, right-click on this role and select Properties, on the tab General tick the boxes IPv4 router, choose LAN and call on demand, and Remote Access IPv4 Server:
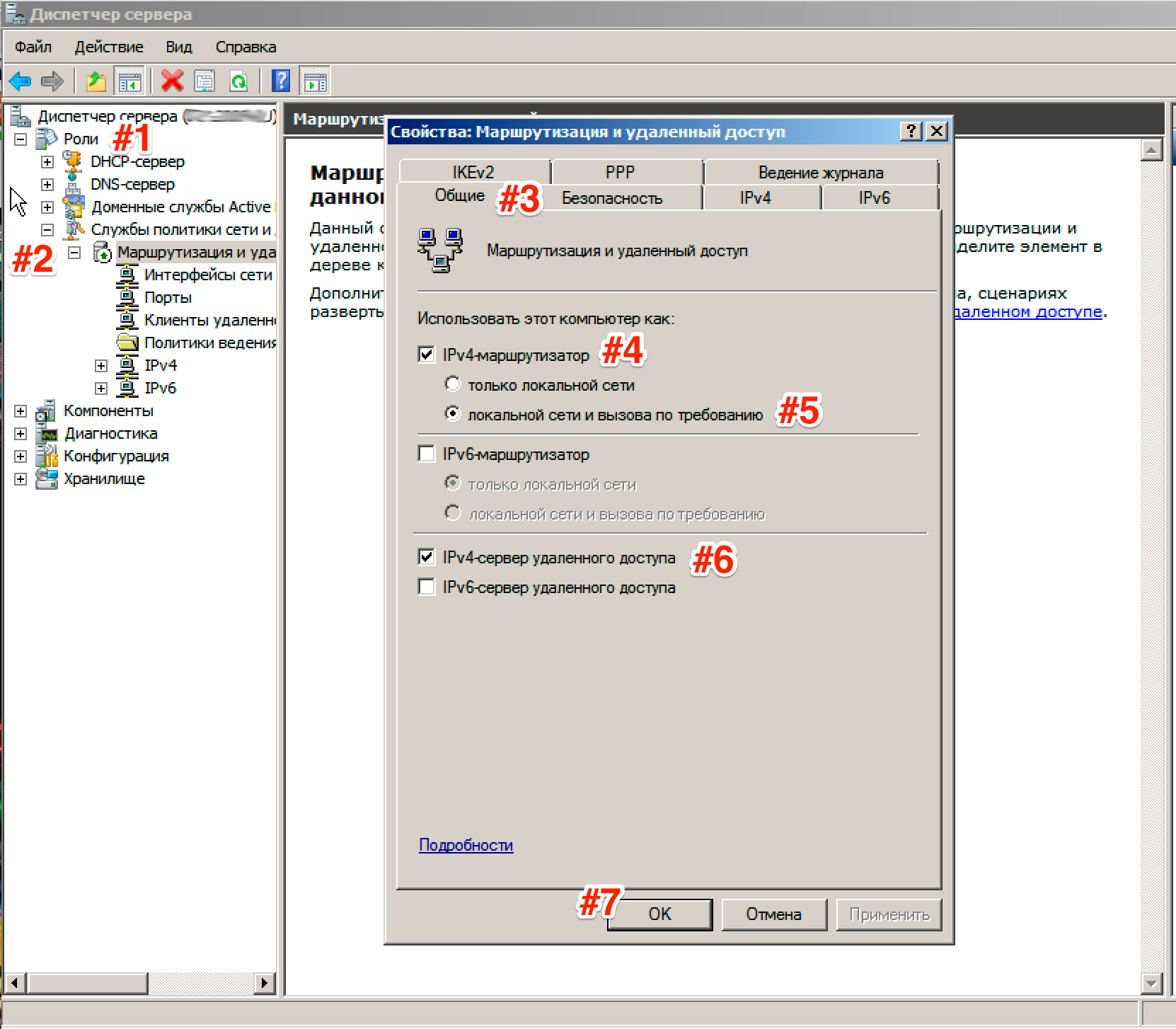
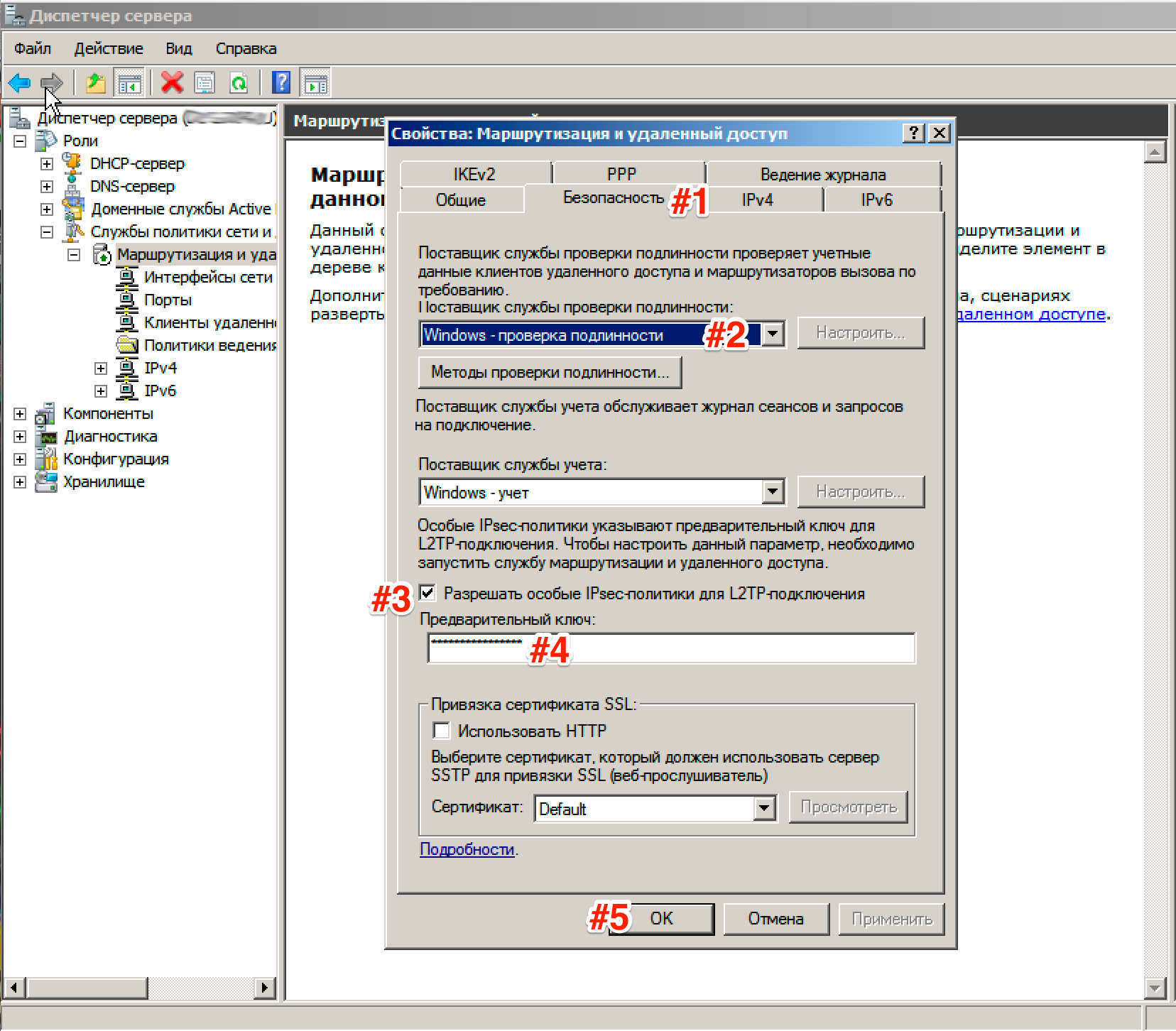
Now we need to enter the preshared key. Go to tab Security and in the field Allow specific IPSec policies for L2TP connection check the box and enter your key. ( About the key. You can enter an arbitrary combination of letters and numbers there. The main principle is that the more complex the combination, the safer and remember or write down this combination, we will still need it.) In the tab Authentication Service Provider select Windows - Authentication.
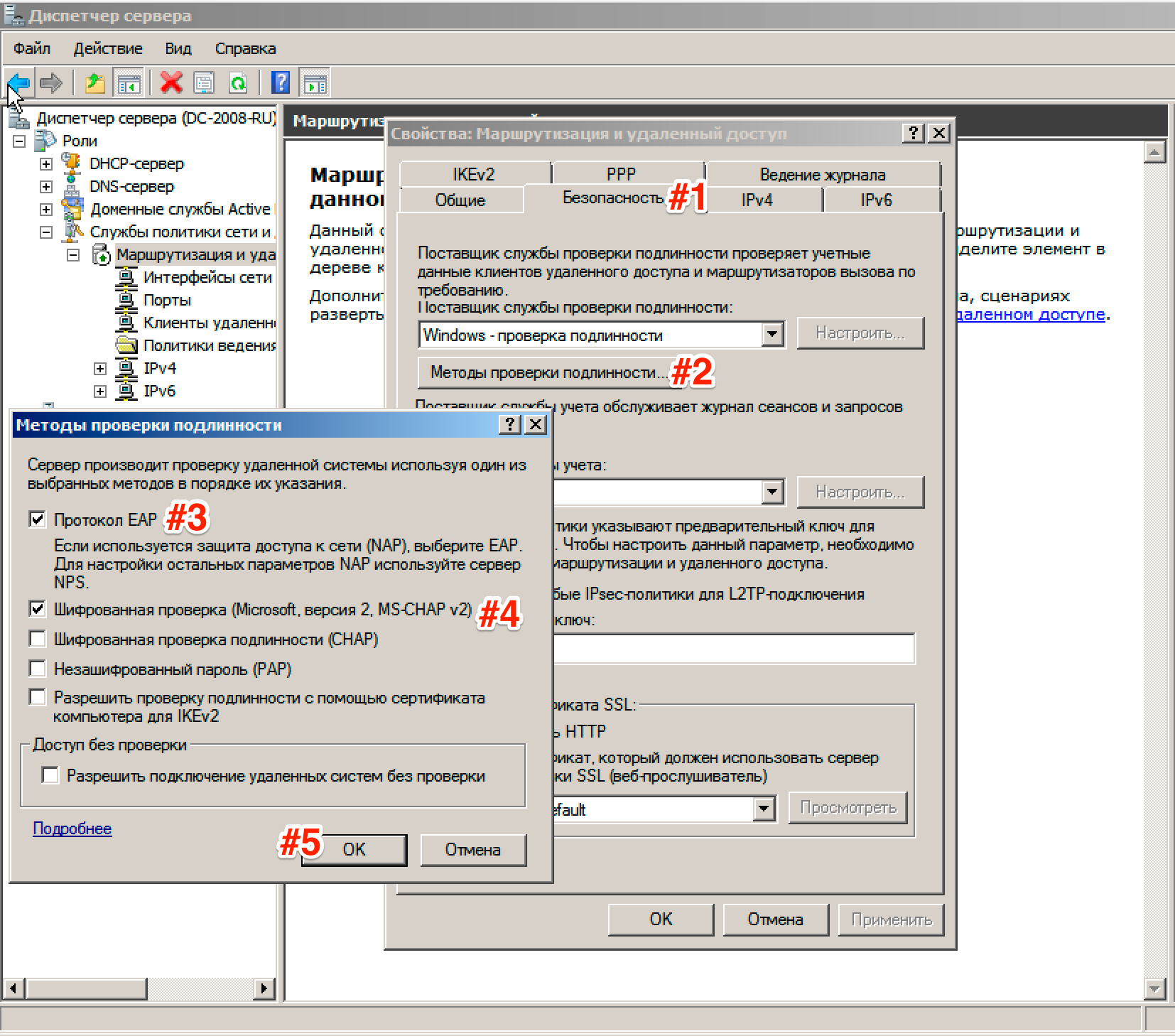
Now we need to set up Connection security. To do this, go to the tab Security and choose Authentication Methods, tick the EAP protocol and Encrypted Verification (Microsoft v2, MS-CHAP v2):
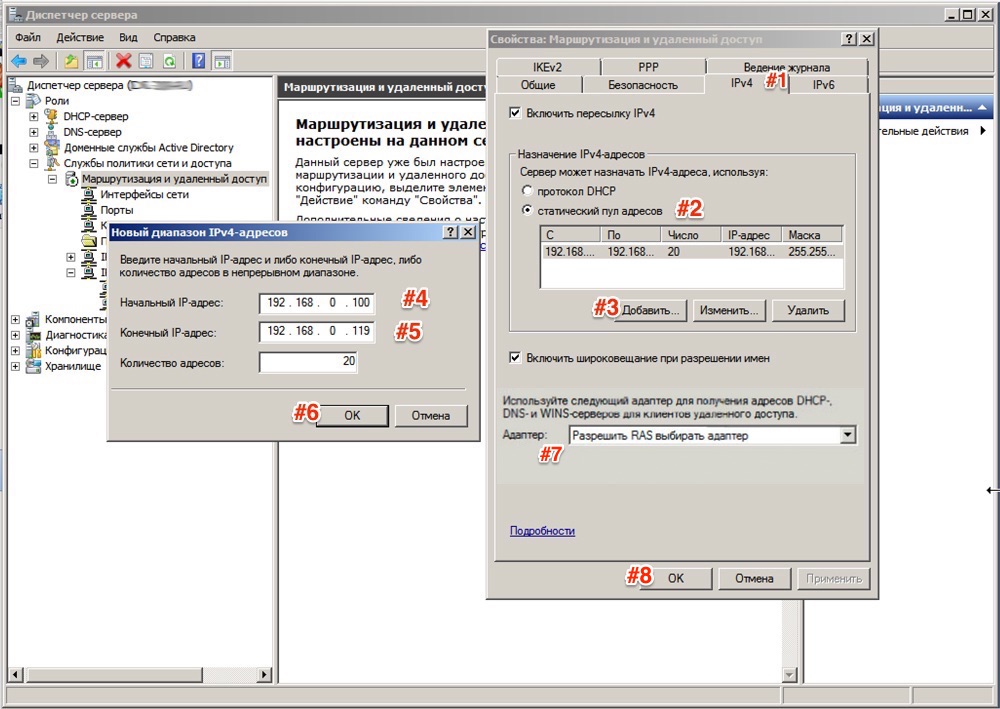
Next, go to the tab IPv4, where we specify which interface will accept connections VPN as well as set up a pool of issued addresses to clients L2TP VPN tab IPv4 (Interface set to Allow RAS to select adapter):
Now let's go to the tab that appears Ports, right click and Properties, choose connection L2TP and press Tune, in a new window put Dial-up connection (incoming only) and Connection on demand (incoming and outgoing) and set the maximum number of ports, the number of ports must match or exceed the expected number of clients. It is better to disable unused protocols by unchecking both checkboxes in their properties.
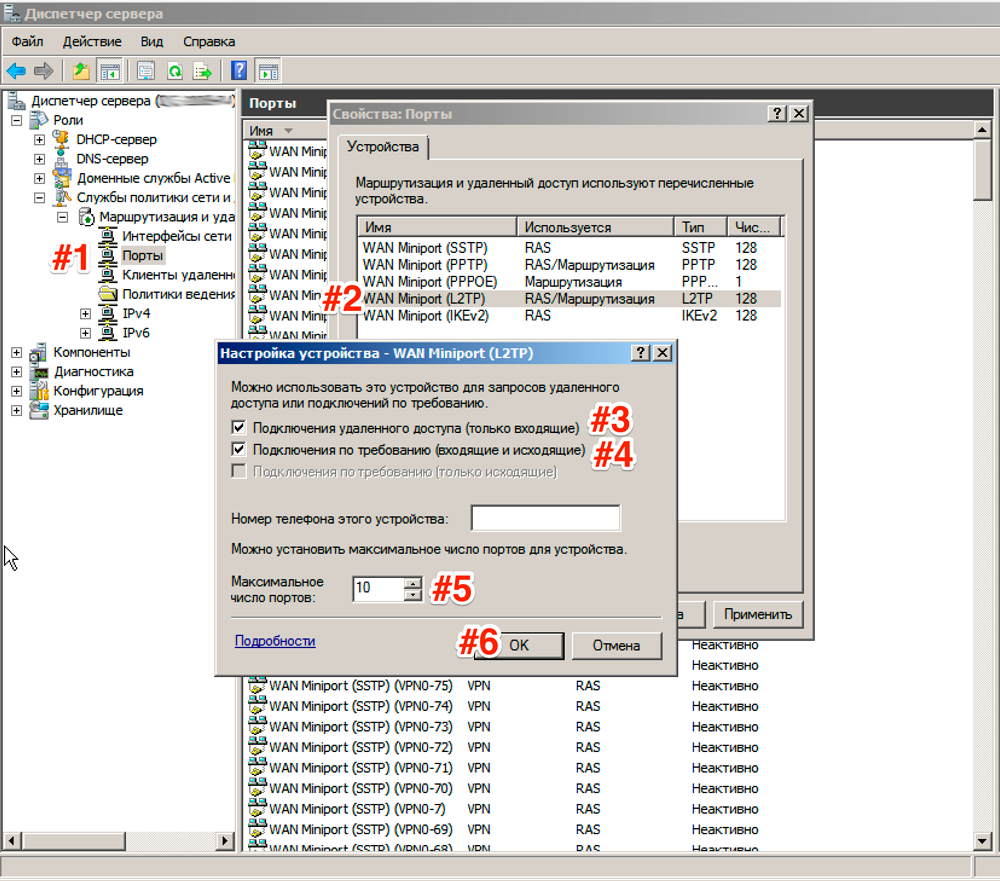
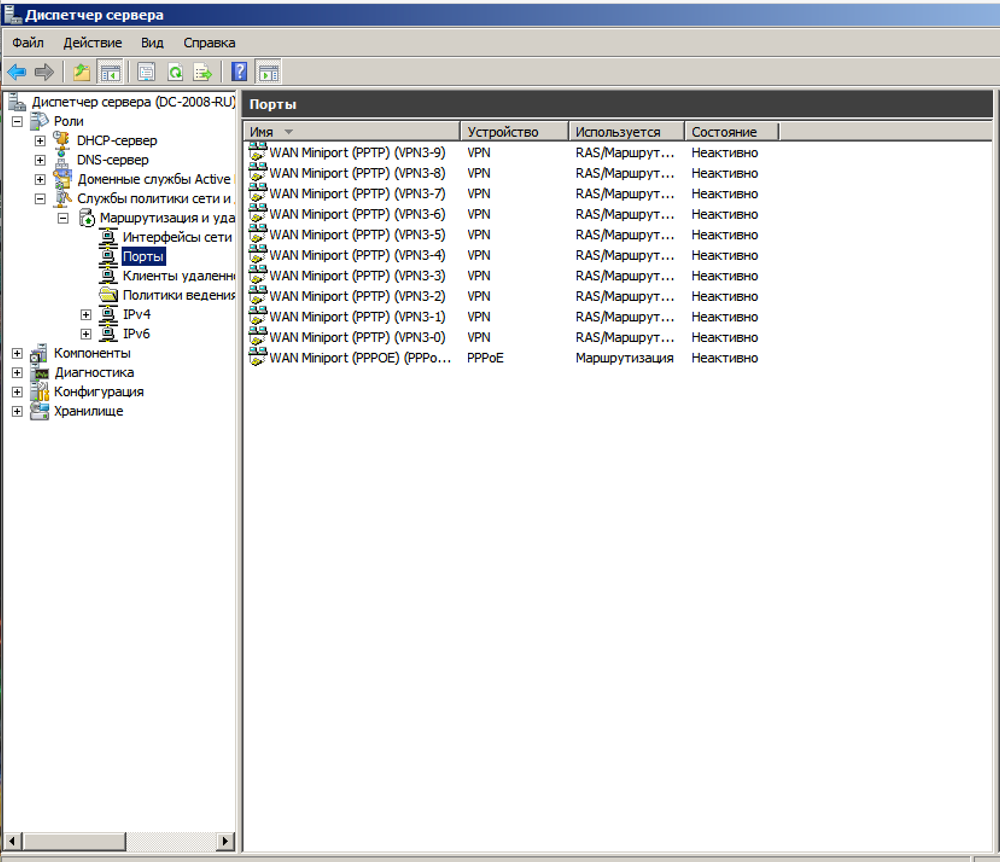
As a result, only the ports you need in the number you specified should remain in your list of ports.
This completes the server setup. It remains only to allow users to connect to the server. Go to Server Manager: Configuration - Local Users and Groups - Users -Select user and right click - Properties. On the tab Incoming calls - Network access rights expose Allow access. (If your server is running Active Directory, then the settings must be entered in the appropriate snap-in)
And do not forget to switch ports on your router, as well as open them in your Firewall:
- IKE - UDP port 500 (Receive\Send)
- L2TP - UDP port 1701 (Receive/Send)
- IPSec ESP - UDP Port 50 (Receive/Send)
- IPSec NAT-T - UDP port 4500 (Receive\Send)



