The purpose of this article is to compare certified firewalls that can be used to protect IPDN. The review considers only certified software products, the list of which was compiled from the FSTEC register of Russia.
Choosing a firewall for a certain level of personal data protection
In this review, we will consider the firewalls presented in Table 1. This table indicates the name of the firewall and its class. This table will be especially useful when selecting software to protect personal data.Table 1. List of firewalls certified by FSTEC
| Software | ME class |
| ME "Blokpost-Ekran 2000/HR" | 4 |
| Special software firewall “Z-2”, version 2 | 2 |
| TrustAccess information security tool | 2 |
| TrustAccess-S information security tool | 2 |
| Firewall StoneGate Firewall | 2 |
| Security Studio Endpoint Protection Personal Firewall | 4 |
| Software package "Security Server CSP VPN Server. Version 3.1" | 3 |
| Software package "Security Gateway CSP VPN Gate.Version 3.1" | 3 |
| Software package “Security Client CSP VPN Client. Version 3.1" | 3 |
| Firewall software package “Ideco ICS 3” | 4 |
| Software package "Traffic Inspector 3.0" | 3 |
| Cryptographic information protection tool “Continent-AP”. Version 3.7 | 3 |
| Firewall "Cybersafe: Firewall" | 3 |
| Software package “Internet gateway Ideco ICS 6” | 3 |
| VipNet Office Firewall | 4 |
All these software products, according to the FSTEC registry, are certified as firewalls.
According to the order of the FSTEC of Russia No. 21 dated February 18, 2013, to ensure levels 1 and 2 of personal data security (hereinafter referred to as PD), firewalls of at least class 3 are used in case of relevance of threats of the 1st or 2nd type or interaction of the information system (IS) ) with international information exchange networks and firewalls of at least class 4 in the case of the relevance of type 3 threats and the absence of interaction between the information system and the Internet.
To ensure level 3 of personal data security, firewalls of at least class 3 (or class 4, if threats of type 3 are relevant and there is no interaction between the information system and the Internet) are suitable. And to ensure level 4 security, the simplest firewalls are suitable - at least class 5. These, however, are not currently registered in the FSTEC register. In fact, each of the firewalls presented in Table 1 can be used to provide 1-3 levels of security, provided that there are no Type 3 threats and there is no interaction with the Internet. If there is a connection to the Internet, then you need a firewall of at least class 3.
Comparison of firewalls
Firewalls have a specific set of functions. So let's see what functions this or that firewall provides (or does not provide). The main function of any firewall is packet filtering based on a specific set of rules. Not surprisingly, all firewalls support this feature.Also, all firewalls reviewed support NAT. But there are quite specific (but no less useful) functions, for example, port masking, load regulation, multi-user operating mode, integrity control, program deployment in ActiveDirectory and remote administration from outside. It’s quite convenient, you see, when a program supports deployment in ActiveDirectory - you don’t need to manually install it on every computer on the network. It is also convenient if the firewall supports remote administration from the outside - you can administer the network without leaving home, which will be important for administrators who are accustomed to performing their functions remotely.
The reader may be surprised that many of the firewalls listed in Table 1 do not support ActiveDirectory deployments, and the same can be said for other features such as load throttling and port masquerading. In order not to describe which firewall supports this or that function, we have systematized their characteristics in Table 2.
Table 2. Firewall capabilities 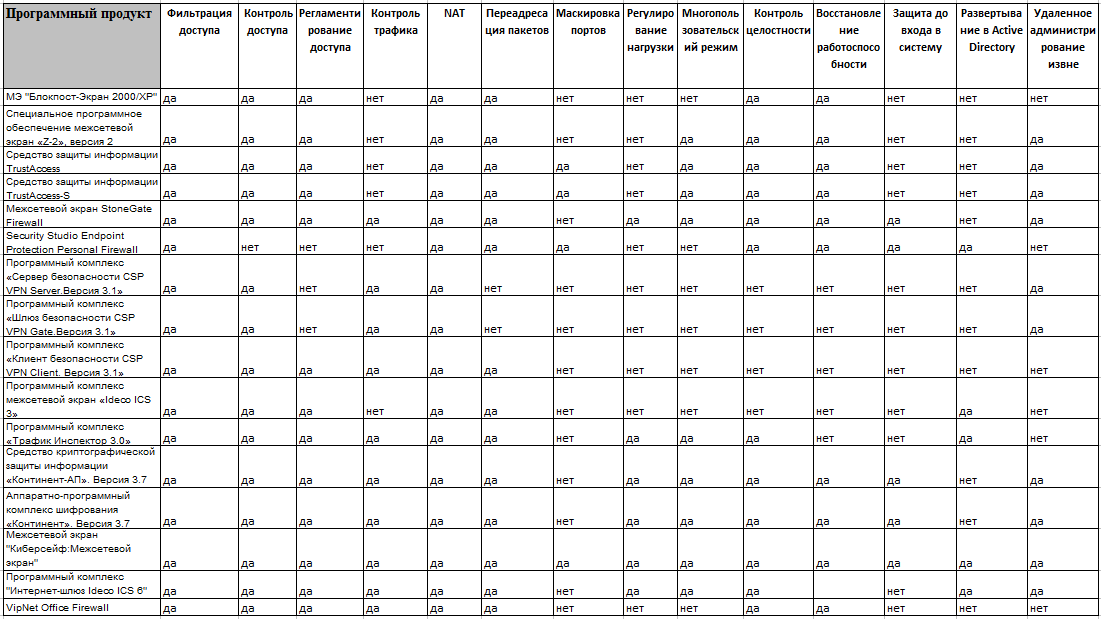
How will we compare firewalls?
The main task of firewalls when protecting personal data is to protect ISPD. Therefore, the administrator often does not care what additional functions the firewall will have. The following factors are important to him:- Protection time. It’s clear here that the faster the better.
- Ease of use. Not all firewalls are equally convenient, as will be shown in the review.
- Price. Often the financial side is decisive.
- Delivery time. Often the delivery time leaves much to be desired, and data needs to be protected now.
All firewalls have approximately the same security, otherwise they would not have a certificate.
Firewalls in review
Next we will compare three firewalls - VipNet Office Firewall, Cybersafe Firewall and TrustAccess.TrustAccess Firewall is a distributed firewall with centralized management, designed to protect servers and workstations from unauthorized access and limit network access to enterprise information systems.
Cybersafe Firewall- a powerful firewall designed to protect computer systems and local networks from external malicious influences.
ViPNet Office Firewall 4.1- a software firewall designed to control and manage traffic and traffic transformation (NAT) between local network segments during their interaction, as well as during the interaction of local network nodes with public network resources.
ISPD protection time
What is the ISPD protection time? Essentially, this is the time it takes to deploy the program to all computers on the network and the time to configure the rules. The latter depends on the ease of use of the firewall, but the former depends on the suitability of its installation package for centralized installation.All three firewalls are distributed as MSI packages, which means you can use ActiveDirectory deployment tools to install them centrally. It would seem that everything is simple. But in practice it turns out that this is not the case.
An enterprise typically uses centralized firewall management. This means that a firewall management server is installed on one computer, and client programs or agents, as they are also called, are installed on the rest. The whole problem is that when installing the agent, you need to set certain parameters - at least the IP address of the management server, and maybe also a password, etc.
Therefore, even if you deploy MSI files to all computers on the network, you will still have to configure them manually. And this would not be very desirable, given that the network is large. Even if you only have 50 computers, just think about it - go to each PC and configure it.
How to solve a problem? And the problem can be solved by creating a transformation file (MST file), also known as a response file, for the MSI file. But neither VipNet Office Firewall nor TrustAccess can do this. This is why, by the way, Table 2 indicates that there is no support for Active Directory deployment. It is possible to deploy these programs in a domain, but manual work by an administrator is required.
Of course, the administrator can use editors like Orca to create the MST file.
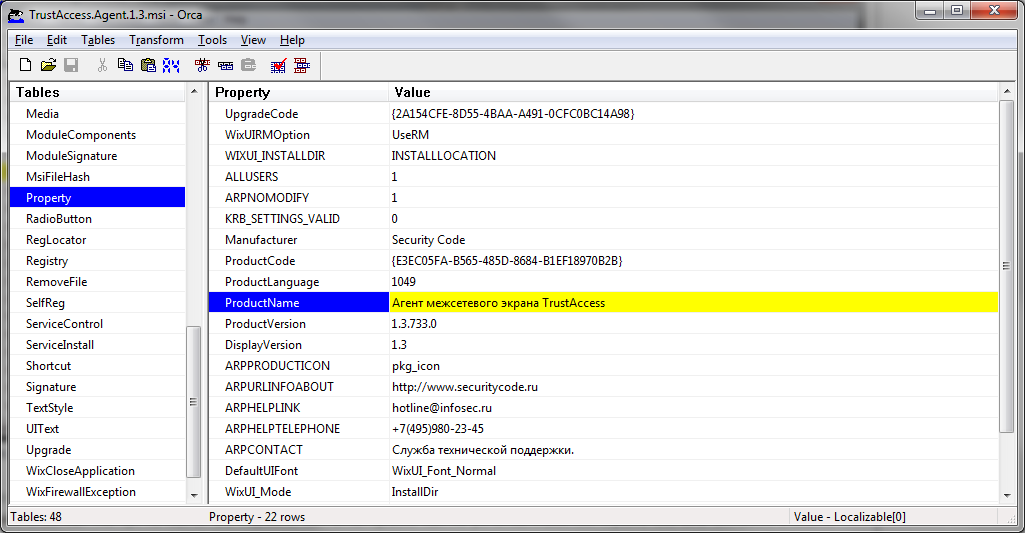
Rice. 1. Orca editor. Trying to create an MST file for TrustAccess.Agent.1.3.msi
But do you really think that everything is so simple? Opened the MSI file in Orca, tweaked a couple of parameters and got a ready-made answer file? Not so! Firstly, Orca itself is not simply installed. You need to download the Windows Installer SDK, extract orca.msi from it using 7-Zip and install it. Did you know about this? If not, then consider that you spent about 15 minutes searching for the necessary information, downloading the software and installing the editor. But all the torment does not end there. The MSI file has many options. Look at fig. 1 - these are only parameters of the Property group. Which one should I change to indicate the server's IP address? You know? If not, then you have two options: either manually configure each computer or contact the developer, wait for a response, etc. Considering that developers sometimes take quite a long time to respond, the actual deployment time of the program depends only on the speed of your movement between computers. It's good if you installed a remote management tool in advance - then deployment will go faster.
Cybersafe Firewall automatically creates an MST file; you just need to install it on one computer, get the coveted MST file and specify it in Group Policy. You can read about how to do this in the article “Separation of information systems when protecting personal data.” In just half a hour (or even less) you can deploy a firewall on all computers on the network.
That is why Cybersafe Firewall receives a rating of 5, and its competitors - 3 (thanks, at least the installers are in MSI format, not .exe).
| Product | Grade |
| VipNet Office Firewall | |
| Cybersafe Firewall | |
| TrustAccess |
Ease of use
A firewall is not a word processor. This is a rather specific software product, the use of which comes down to the “install, configure, forget” principle. On the one hand, ease of use is a secondary factor. For example, iptables in Linux cannot be called convenient, but they still use it? On the other hand, the more convenient the firewall, the faster it will be possible to protect the ISPD and perform some functions for its administration.Well, let's see how convenient the firewalls in question are in the process of creating and protecting ISDN.
We'll start with VipNet Office Firewall, which, in our opinion, is not very convenient. You can select computers into groups only by IP addresses (Fig. 2). In other words, there is a binding to IP addresses and you need to either allocate different ISPDs to different subnets, or split one subnet into ranges of IP addresses. For example, there are three ISPDs: Management, Accounting, IT. You need to configure the DHCP server so that computers in the Management group are “distributed” IP addresses from the range 192.168.1.10 - 192.168.1.20, Accounting 192.168.1.21 - 192.168.1.31, etc. This is not very convenient. It is for this that one point will be deducted from VipNet Office Firewall.
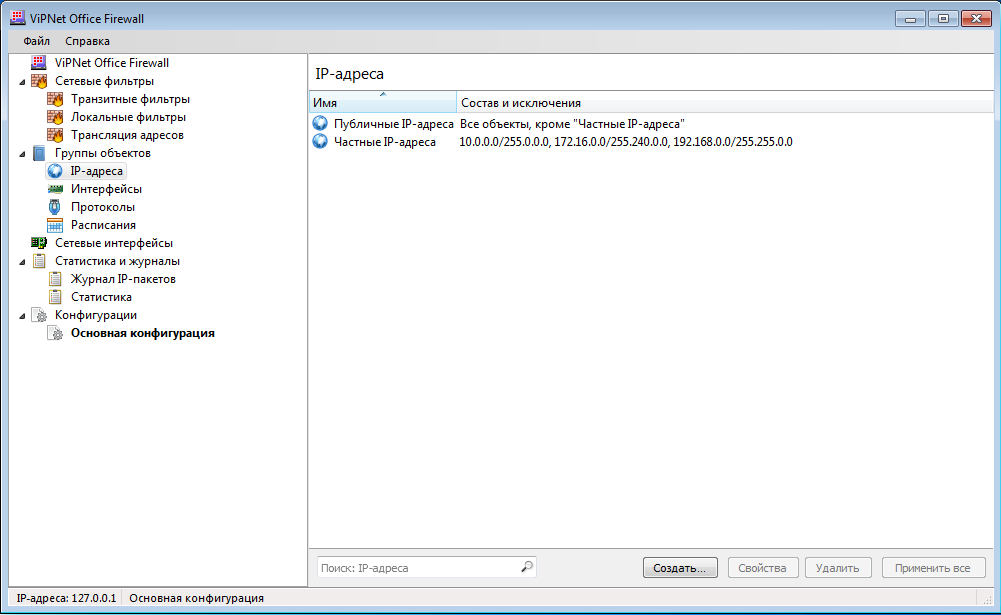
Rice. 2. When creating groups of computers, there is an obvious binding to the IP address
In the Cybersafe firewall, on the contrary, there is no binding to the IP address. Computers that are part of a group can be located in different subnets, in different ranges of the same subnet, and even located outside the network. Look at fig. 3. The company's branches are located in different cities (Rostov, Novorossiysk, etc.). Creating groups is very simple - just drag the names of computers into the desired group and click the button Apply. After this you can click the button Set the rules to form rules specific to each group.
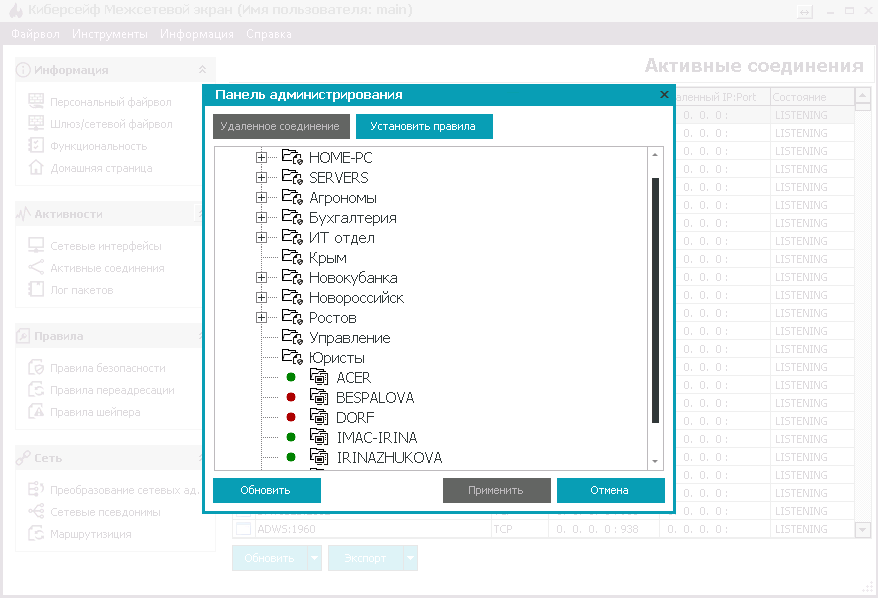
Rice. 3. Managing groups in Cybersafe Firewall
As for TrustAccess, it should be noted that it is closely integrated with the system itself. Already created system groups of users and computers are imported into the firewall configuration, which makes it easier to manage the firewall in an ActiveDirectory environment. You don't have to create an ISDN in the firewall itself, but use existing groups of computers in the Active Directory domain.
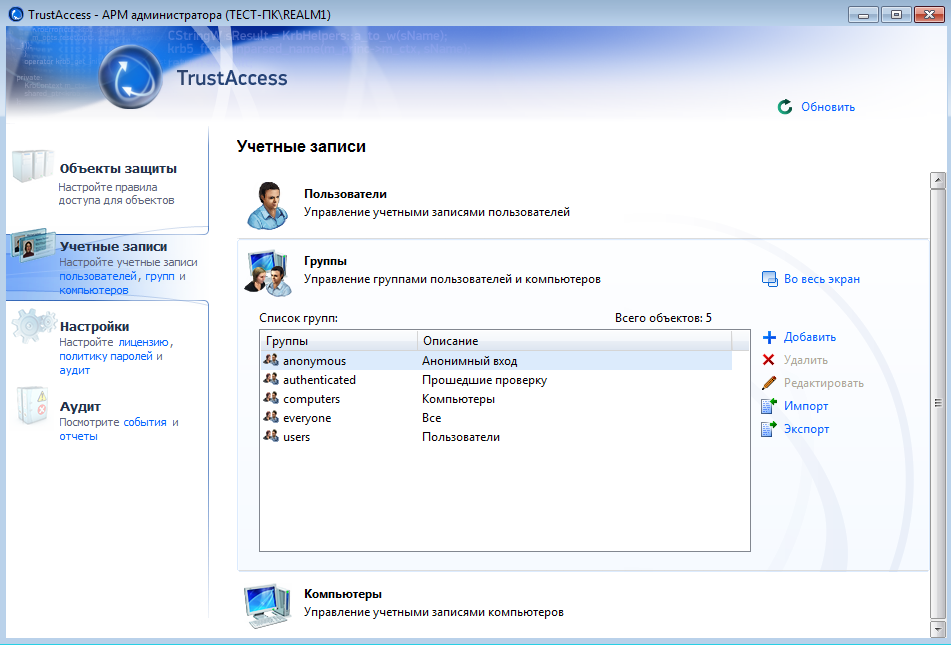
Rice. 4. Groups of users and computers (TrustAccess)
All three firewalls allow you to create so-called schedules, thanks to which the administrator can configure the passage of packets according to a schedule, for example, deny access to the Internet during non-working hours. In VipNet Office Firewall, schedules are created in the section Schedules(Fig. 5), and in Cybersafe Firewall, the rule operating time is set when defining the rule itself (Fig. 6).
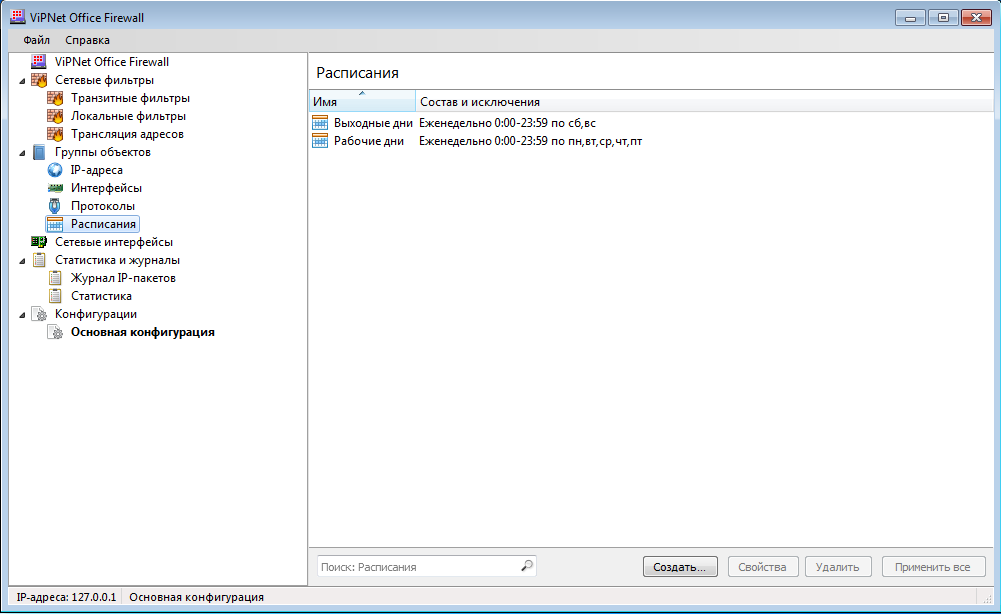
Rice. 5. Schedules in VipNet Office Firewall
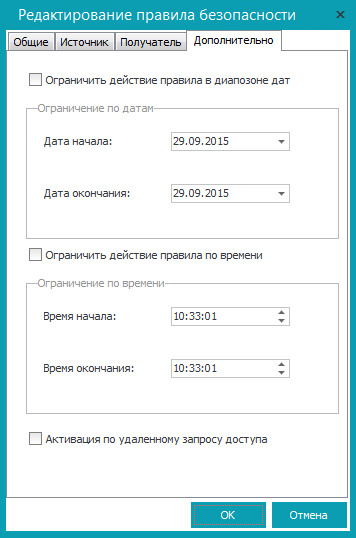
Rice. 6. Rule operating time in Cybersafe Firewall
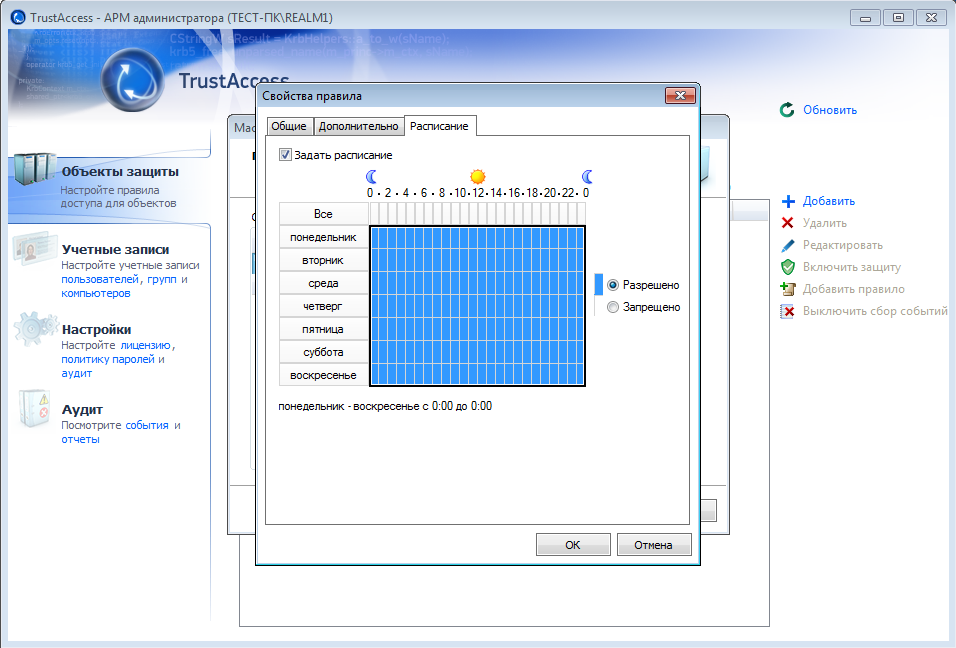
Rice. 7. Schedule in TrustAccess
All three firewalls provide very convenient tools for creating the rules themselves. TrustAccess also provides a convenient rule creation wizard.
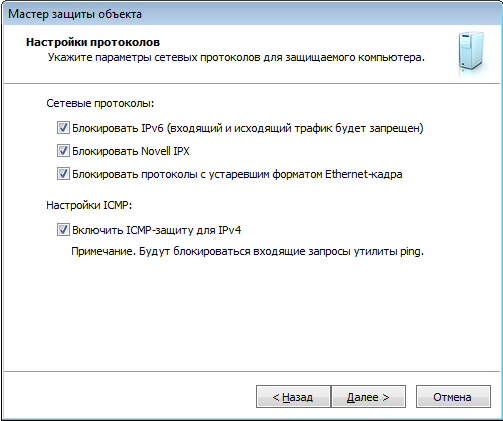
Rice. 8. Creating a rule in TrustAccess
Let's take a look at another feature - tools for receiving reports (magazines, logs). In TrustAccess, to collect reports and information about events, you need to install an event server (EventServer) and a report server (ReportServer). This is not a flaw, but rather a feature (“feature”, as Bill Gates said) of this firewall. As for the Cybersafe and VipNet Office firewalls, both firewalls provide convenient tools for viewing the IP packet log. The only difference is that Cybersafe Firewall first displays all packets, and you can filter out the ones you need using the filter capabilities built into the table header (Fig. 9). And in VipNet Office Firewall, you first need to install filters, and then view the result.
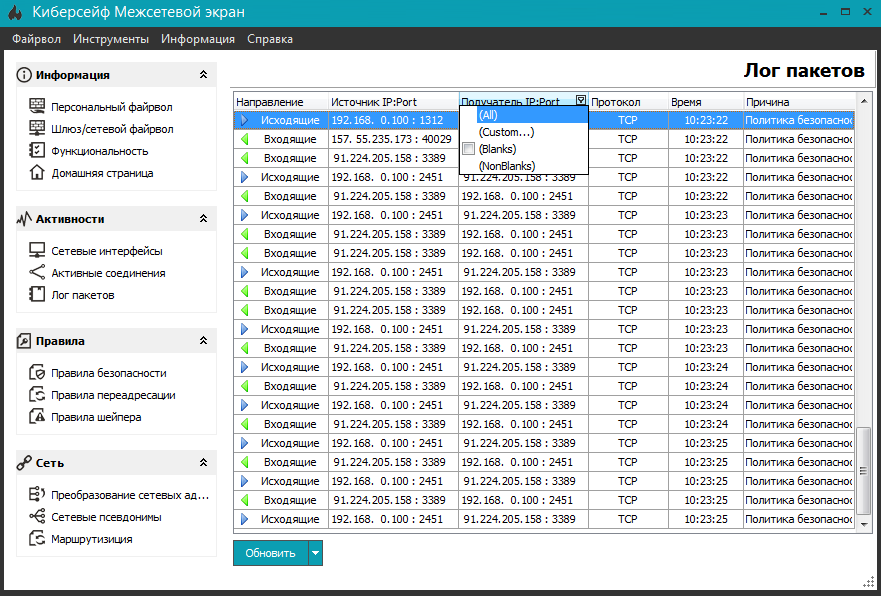
Rice. 9. Managing the log of IP packets in Cybersafe Firewall
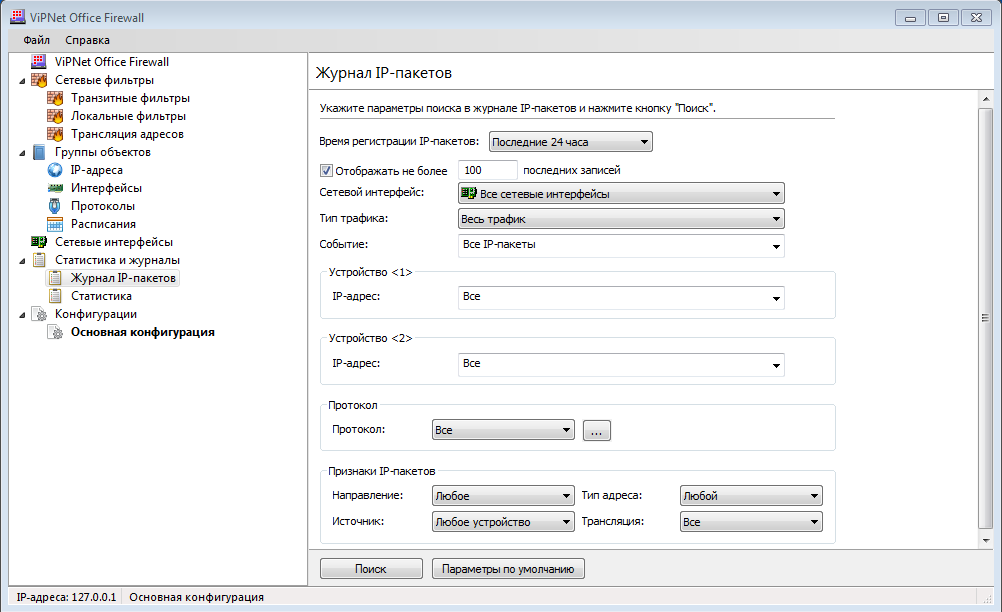
Rice. 10. Managing the IP packet log in VipNet Office Firewall
The Cybersafe firewall had to be deducted 0.5 points for the lack of a log export function to Excel or HTML. The function is far from critical, but sometimes it is useful to simply and quickly export several lines from the log, for example, for “debriefing”.
So, the results of this section:
| Product | Grade |
| VipNet Office Firewall | |
| Cybersafe Firewall | |
| TrustAccess |
Price
It is simply impossible to bypass the financial side of the issue, because it often becomes decisive when choosing a particular product. Thus, the cost of one ViPNet Office Firewall 4.1 license (license for 1 year for 1 computer) is 15,710 rubles. And the cost of a license for 1 server and 5 TrustAccess workstations will cost 23,925 rubles. You can find out the cost of these software products using the links at the end of the article.Remember these two numbers: 15,710 rubles. for one PC (per year) and 23,925 rub. for 1 server and 5 PCs (per year). And now attention: for this money you can buy a license for 25 nodes Cybersafe Firewall (15,178 rubles) or add a little and it will be quite enough for a license for 50 nodes (24,025 rubles). But the most important thing about this product is not the cost. The most important thing is the validity period of the license and technical support. The license for Cybersafe Firewall is without expiration date, as is technical support. That is, you pay once and receive a software product with a lifetime license and technical support.
| Product | Grade |
| VipNet Office Firewall | |
| Cybersafe Firewall | |
| TrustAccess |
Delivery time
In our experience, the delivery time for VipNet Office Firewall is about 2-3 weeks after contacting Infotex OJSC. Honestly, this is quite a long time, considering that you are buying a software product, not a software package.TrustAccess delivery time, if ordered through Softline, is from 1 day. A more realistic period is 3 days, taking into account some delay of Softline. Although they can deliver in 1 day, it all depends on the workload of Softline. Again, this is personal experience; the actual deadline for a specific customer may differ. But in any case, the delivery time is quite low, which cannot be ignored.
As for the CyberSafe Firewall software product, the manufacturer guarantees delivery of the electronic version within 15 minutes after payment.
| Product | Grade |
| VipNet Office Firewall | |
| Cybersafe Firewall | |
| TrustAccess |
What to choose?
If you focus only on the cost of the product and technical support, then the choice is obvious - Cybersafe Firewall. Cybersafe Firewall has an optimal functionality/price ratio. On the other hand, if you need Secret Net support, then you need to look towards TrustAccess. But we can only recommend VipNet Office Firewall as a good personal firewall, but for these purposes there are many other, and also free, solutions.Review carried out by specialists
integrator company DORF LLC